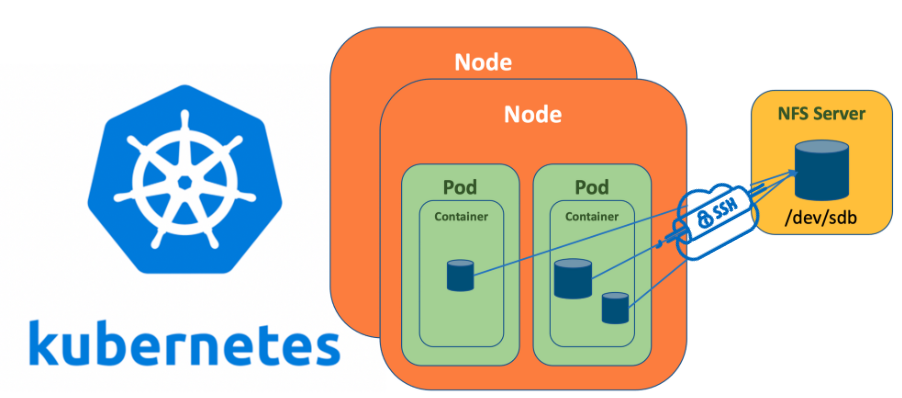
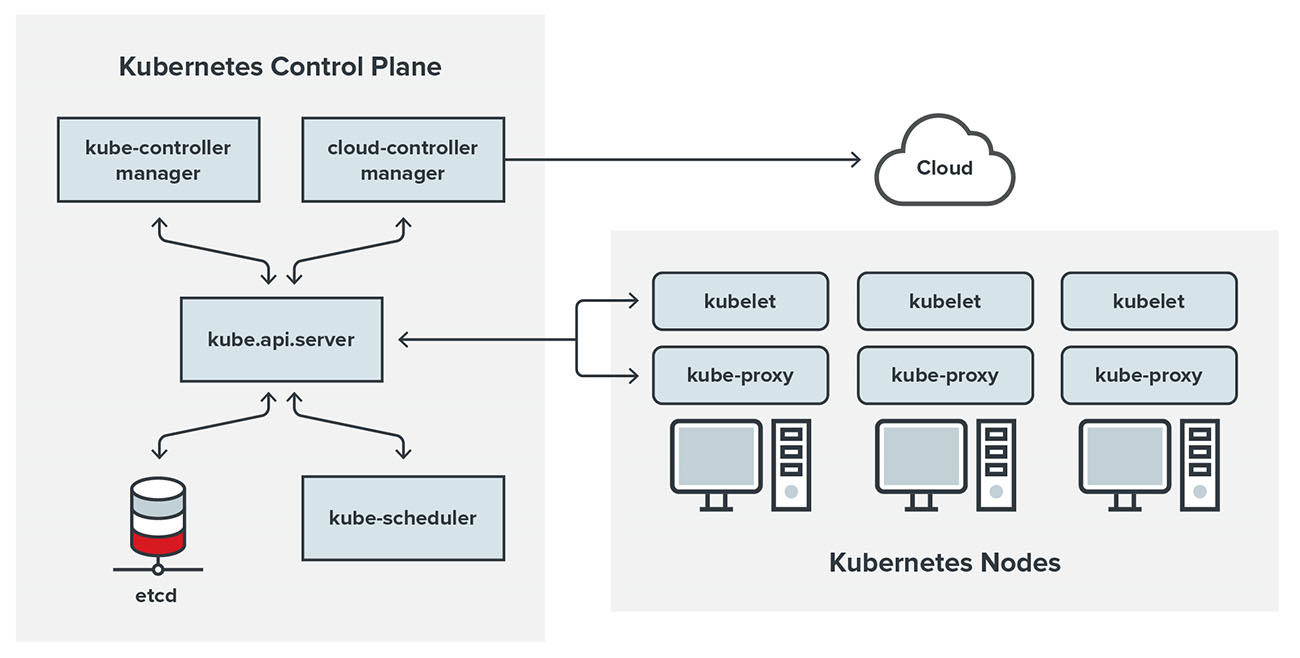
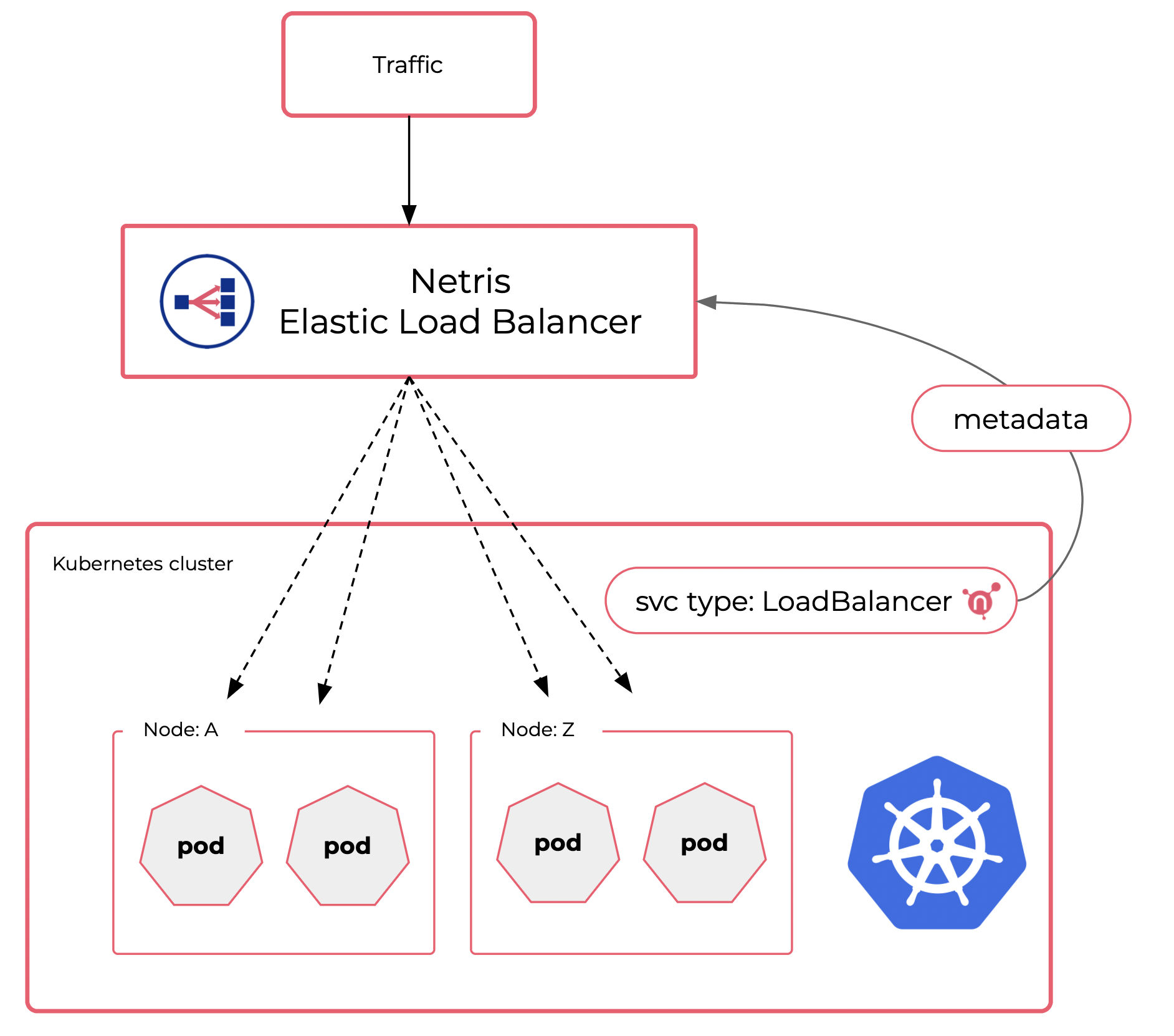
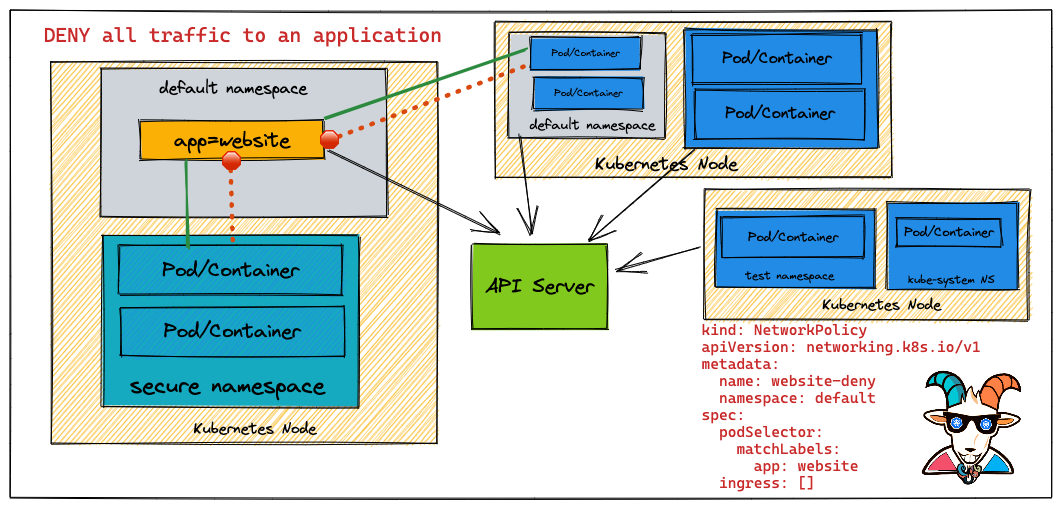
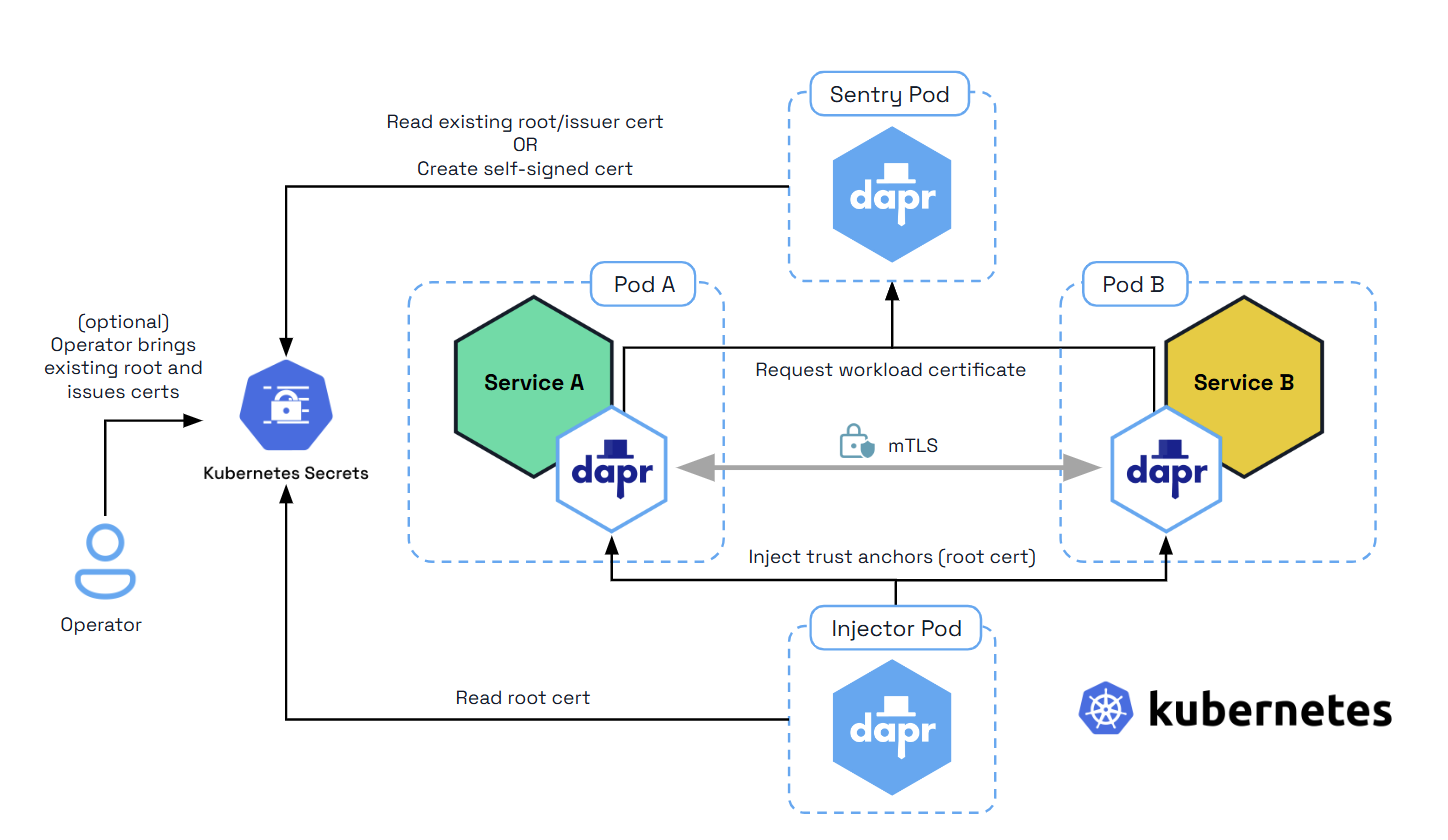
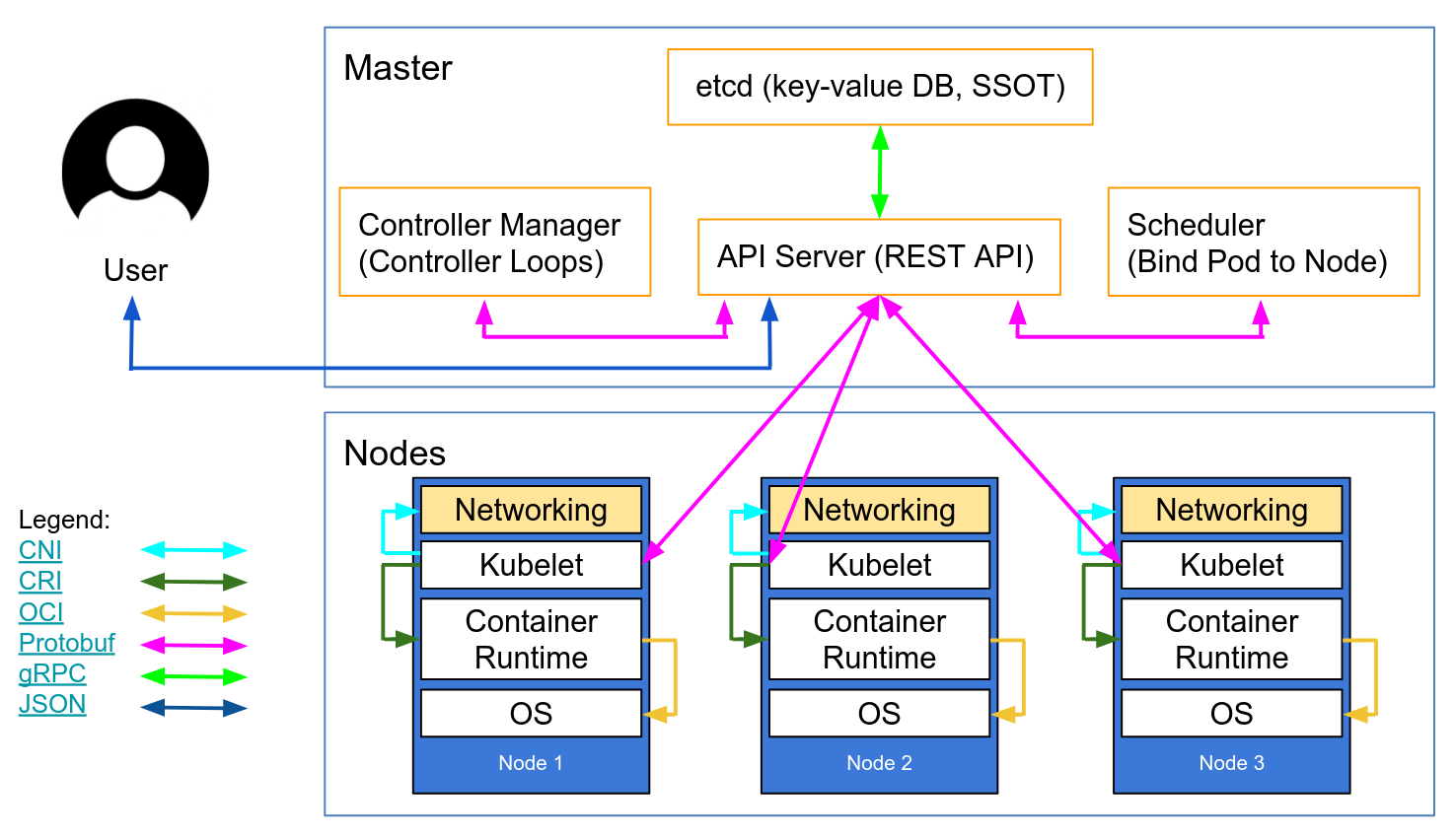
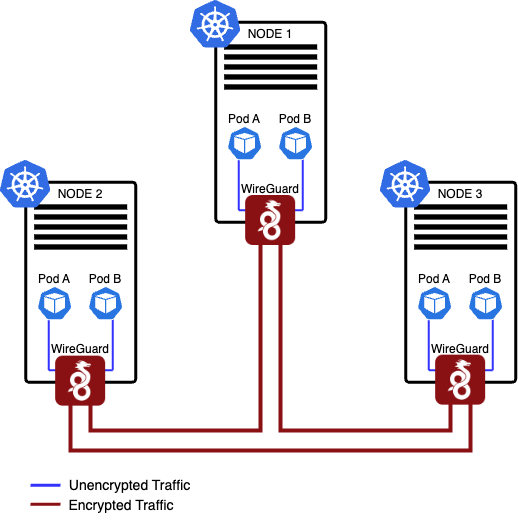
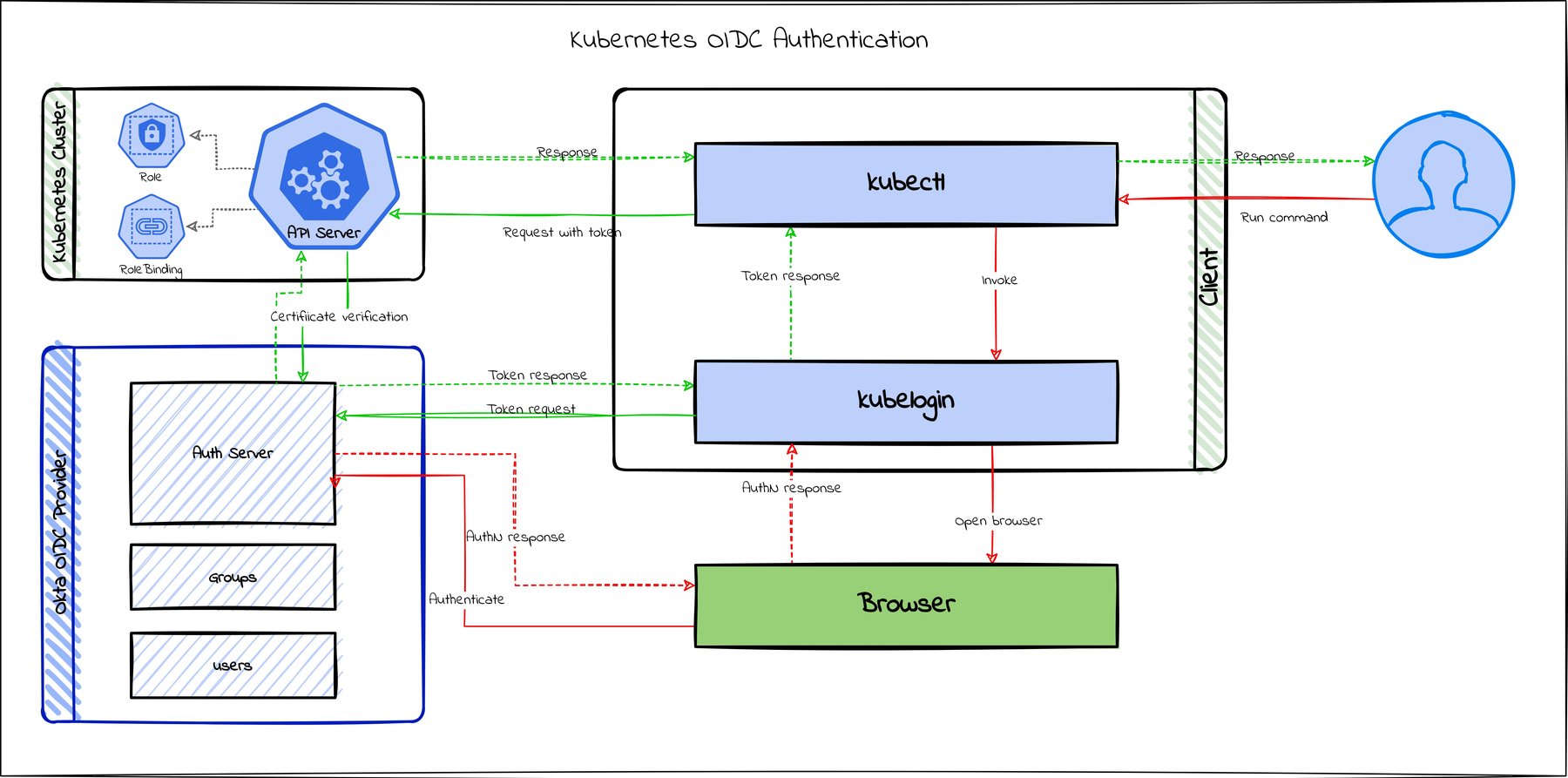
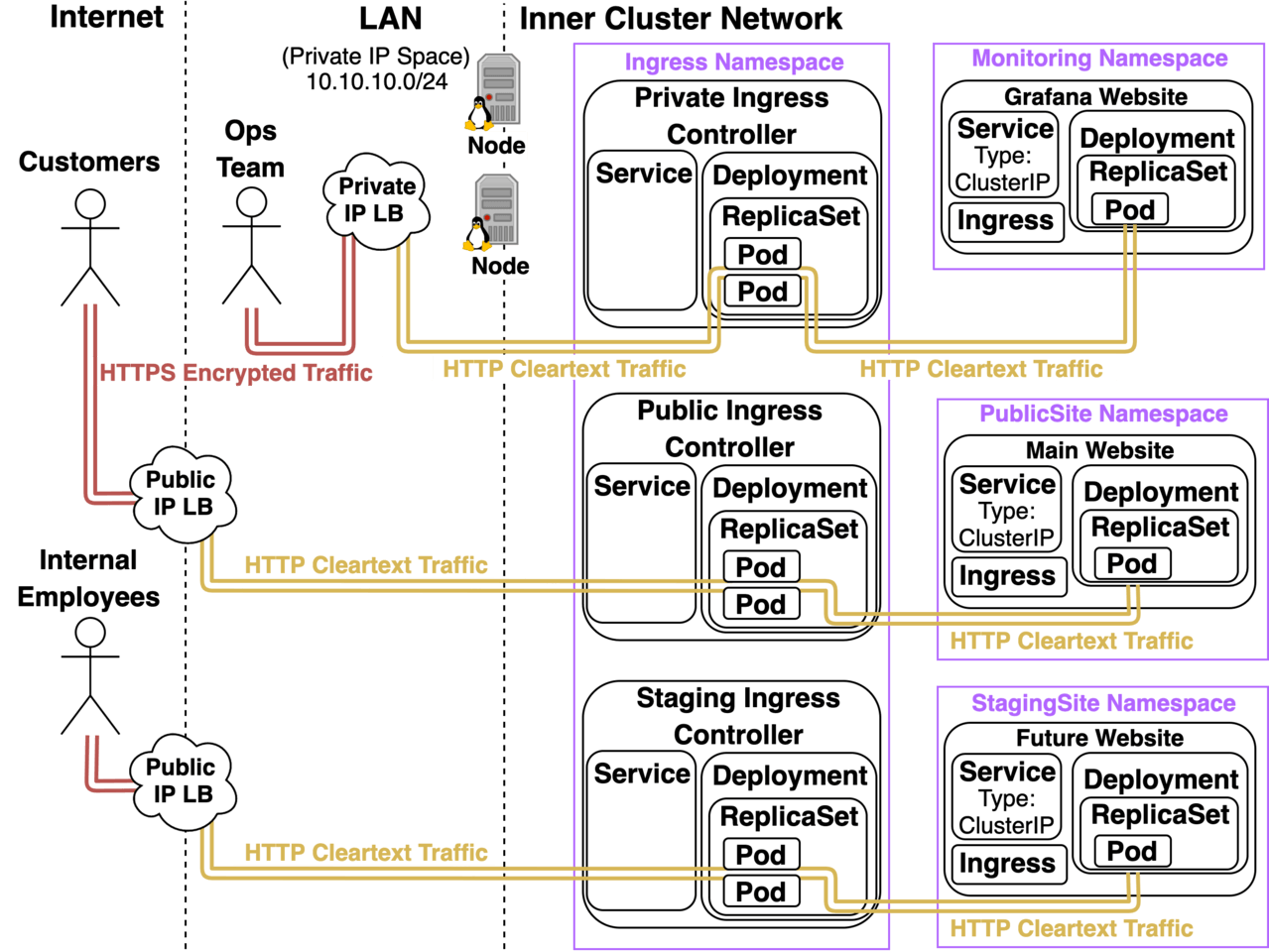
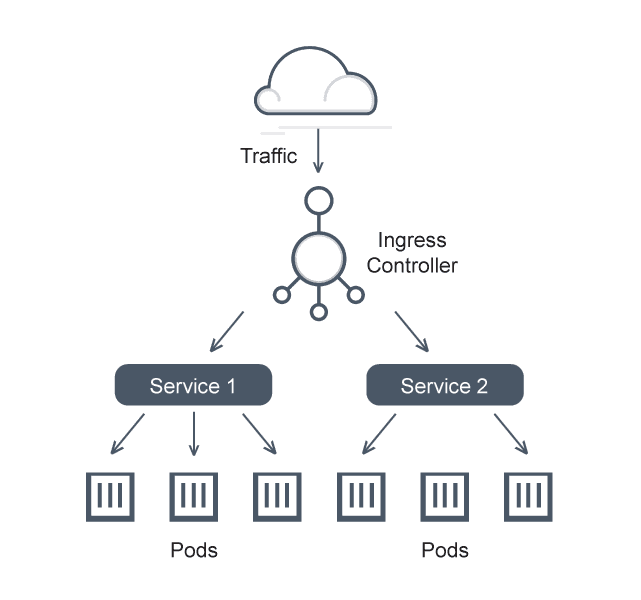
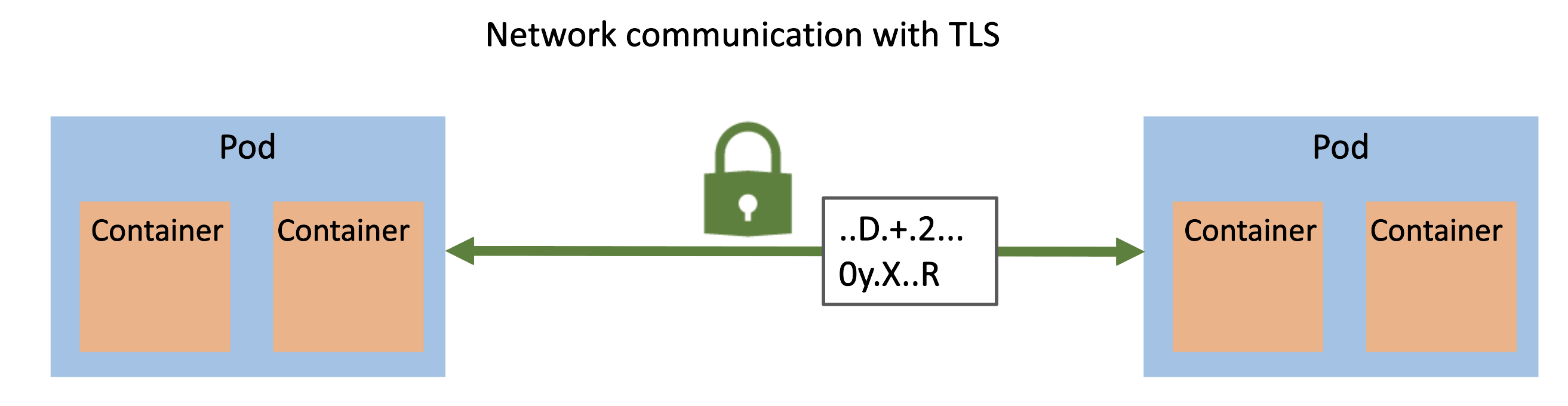
East-West Communication in Kubernetes — How do services communicate within a cluster? | by Abhinav Kapoor | CodeX | Medium
Kubernetes network security foundations: Get started on building your Kubernetes network security policies with Calico!

Setting up end-to-end TLS encryption on Amazon EKS with the new AWS Load Balancer Controller | Containers
IPsec encryption configuration - OVN-Kubernetes default CNI network provider | Networking | OpenShift Container Platform 4.10