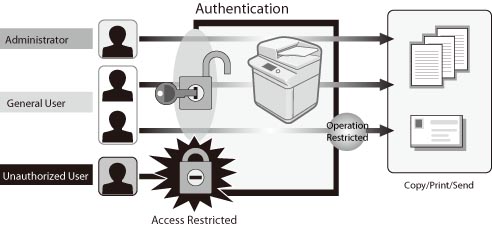
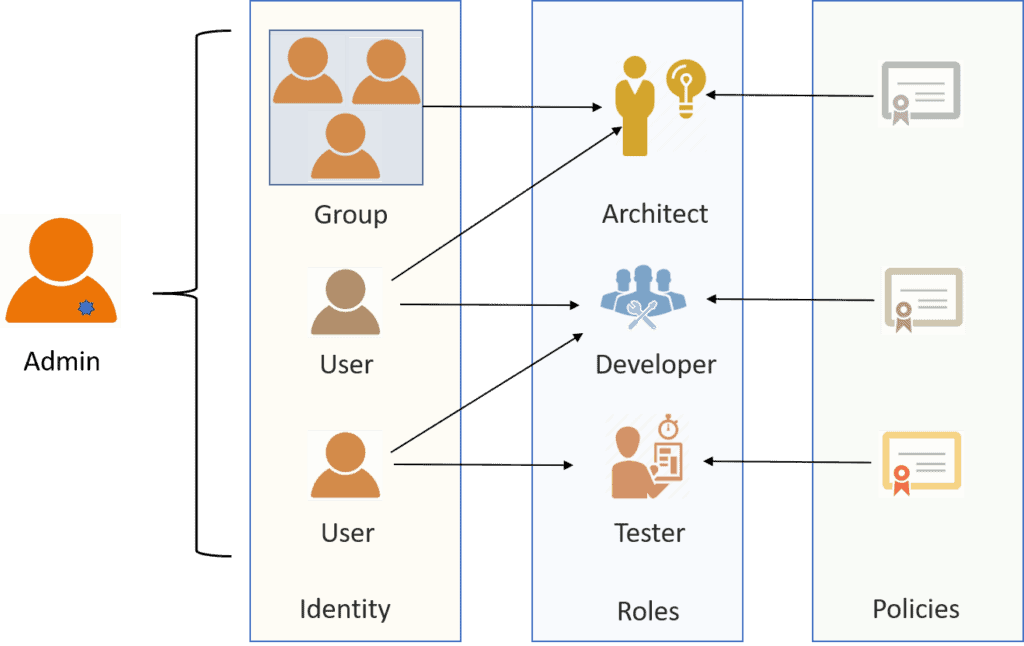
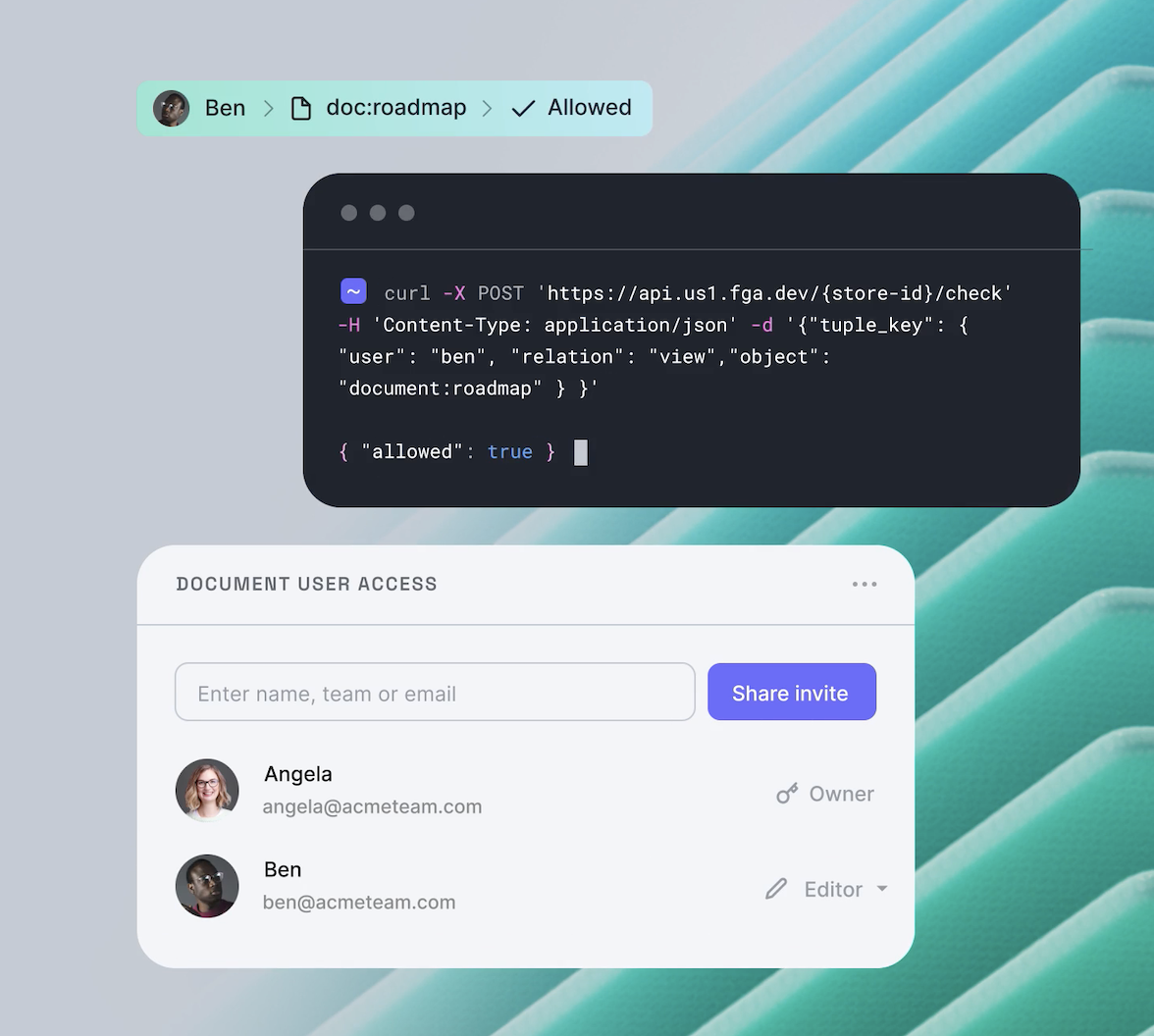
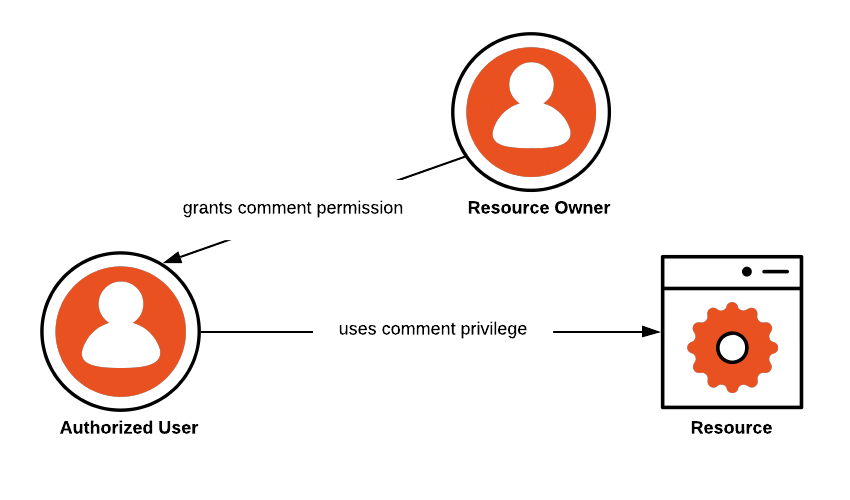
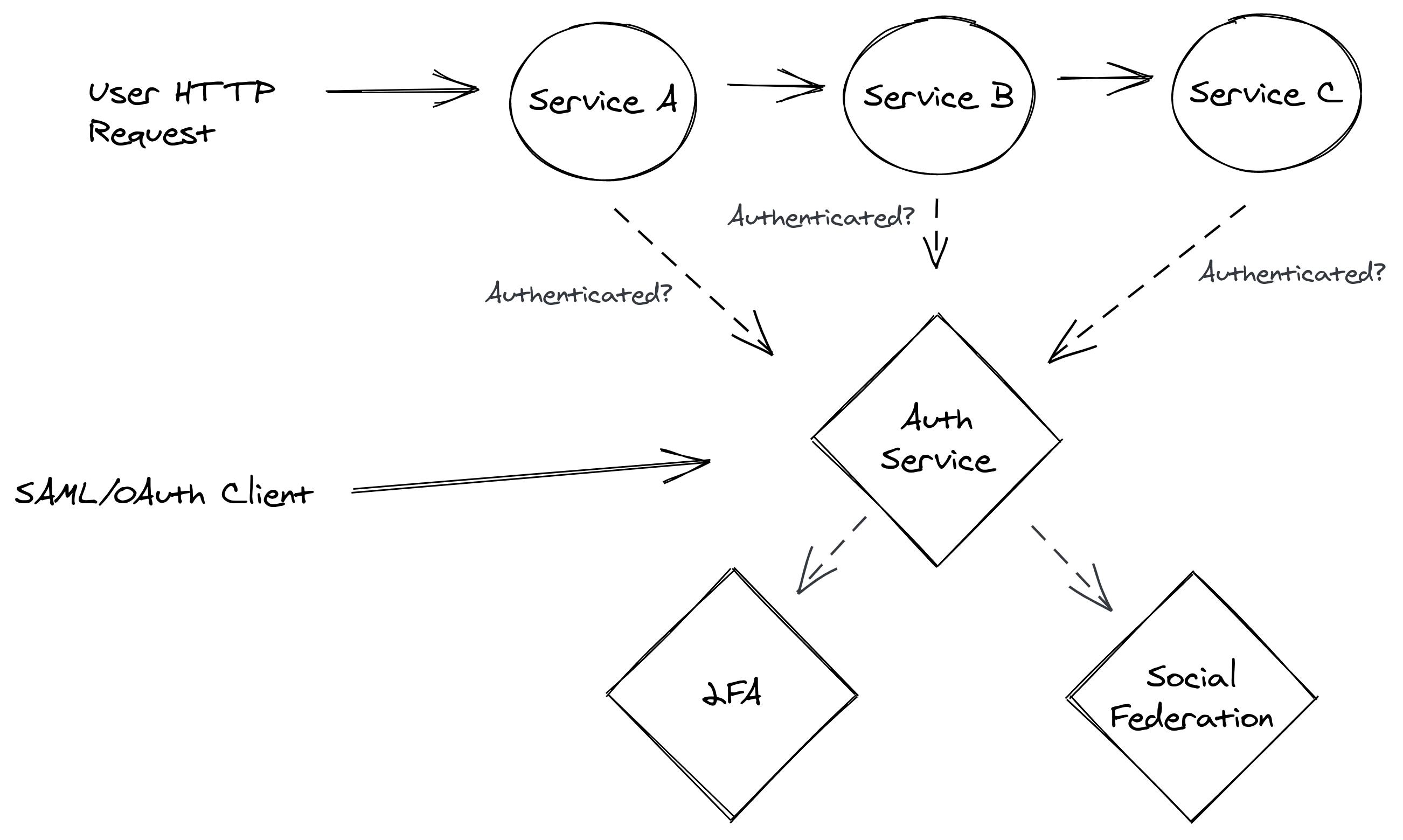
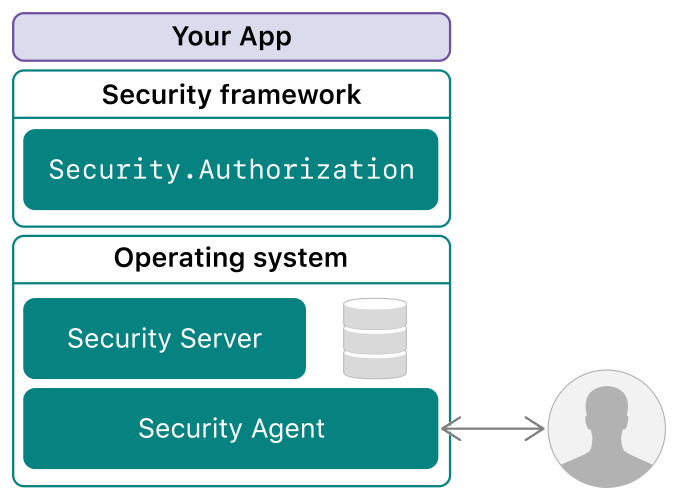
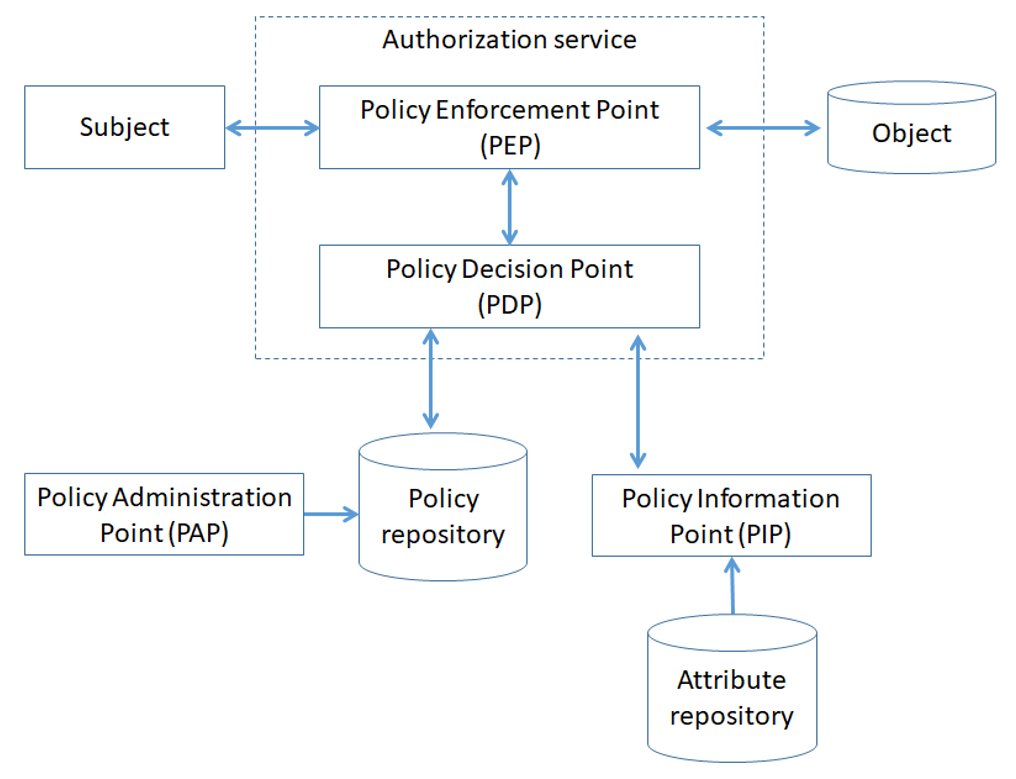
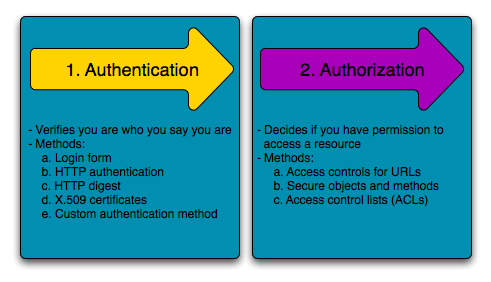
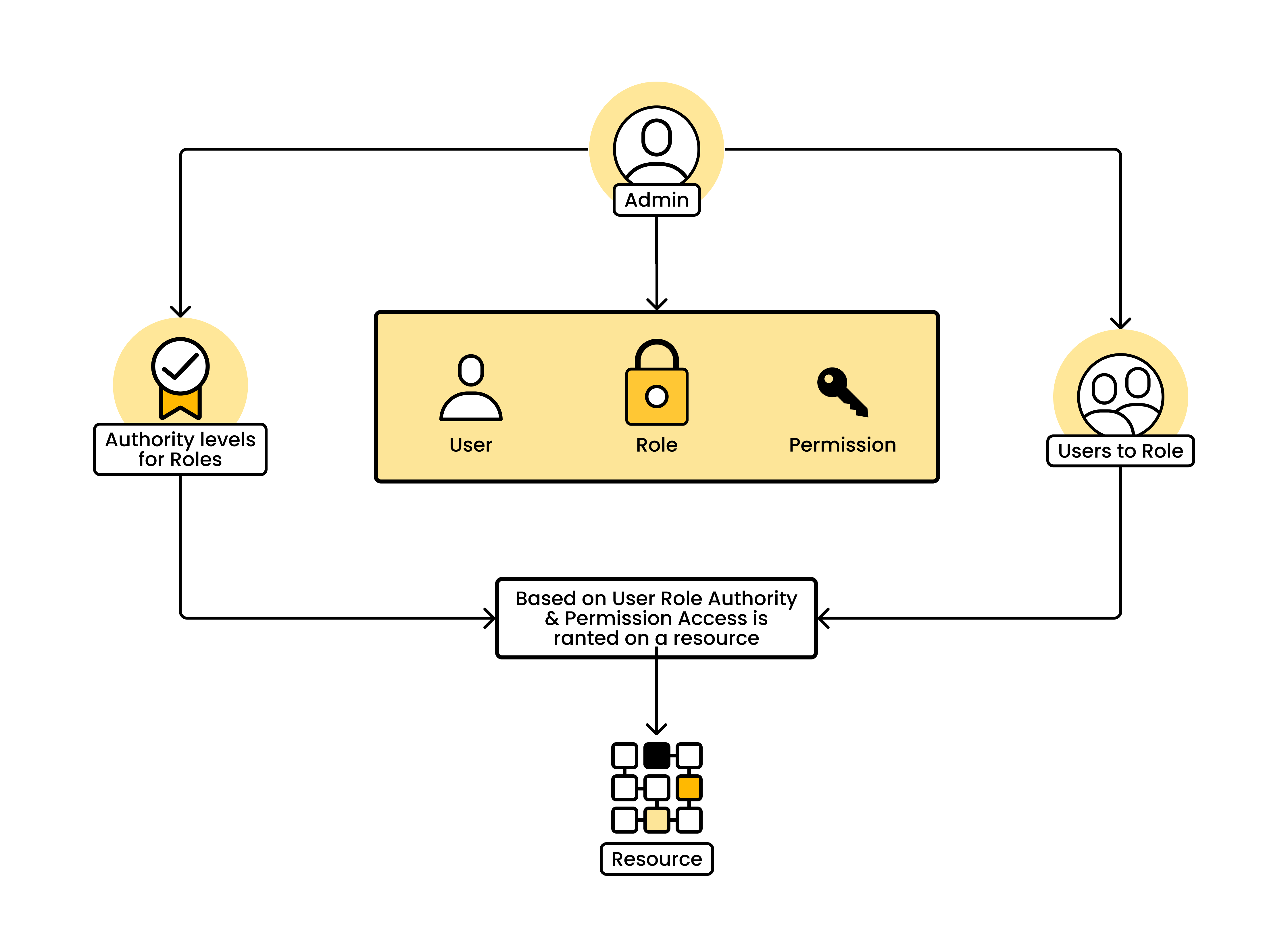
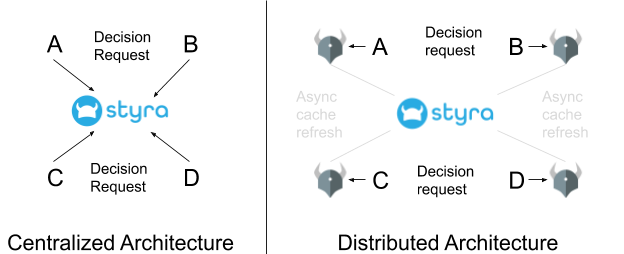
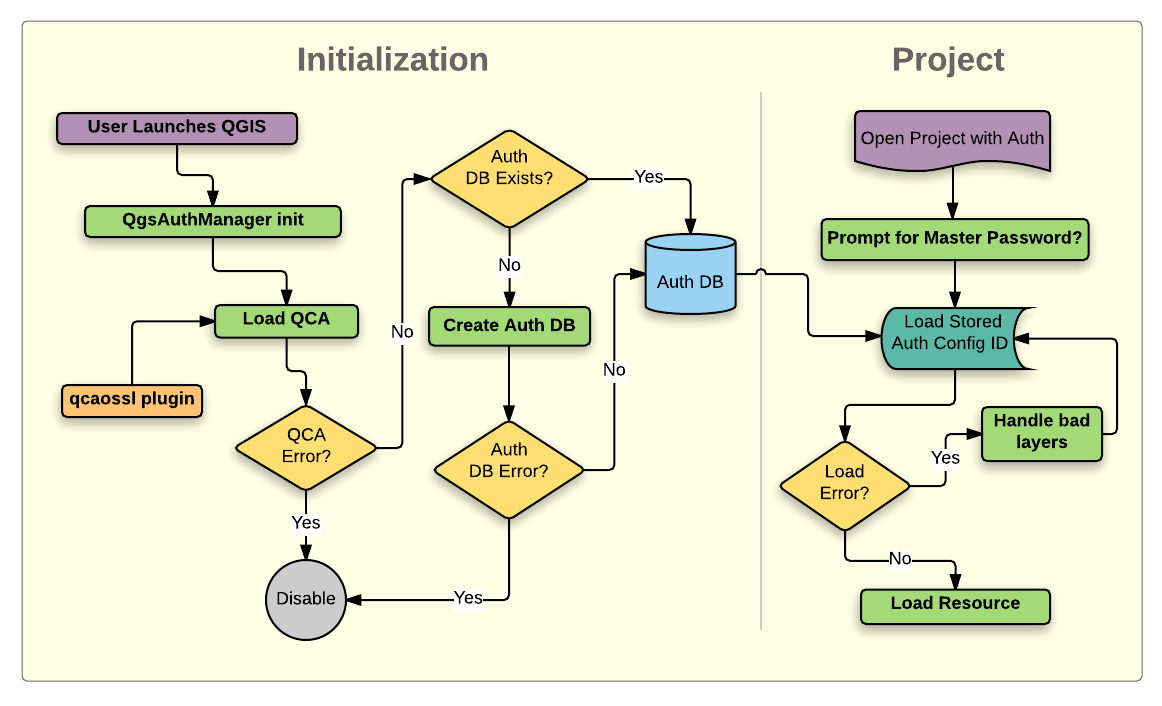
The architecture of the authentication and authorization system based... | Download Scientific Diagram

Amazon.fr - SAP Authorization System: Design and Implementation of Authorization concepts for SAP R/3 and SAP Enterprise Portals - IBM Business Consulting - Livres